Regular scams, revisited.
Posted on: 29 September 2016
By: wolfeg
No Comments »
Filed under: Uncategorized
This month, after taking a break from his blog last month, Graeme Wolfe, our Information and IT Security Officer, takes a further look at the scams that continue to pop up at regular intervals.
Last year I published the blog post ‘Scam merry go round‘ and it would appear that we have saddled up our horses and are back on the scam merry-go-round again.
I was advised by the Student Union Financial Advisors of a scam that told students they could apply for a grant. When they clicked on the link, guess what they were asked for? All their financial and personal details of course. Just what any cyber-criminal would want to help them empty your bank account or steal your identity.
Recently, there was a programme on BBC ‘Inside Out – London’ which identified criminal gangs who used international student’s bank accounts to launder their money. Although it is not directly a scam, it is illegal, and can also leave those students open to scams and fraud in the future.
I’m sure that this won’t be the last of such attempts to defraud students and staff of their money and identity, so be cautious if someone is asking you for those details and check your accounts regularly for unusual activity.
Just like the ‘419’ scams, do you really think that someone in a foreign country has specifically selected you to help them move millions of pounds or dollars around? Only to send you a badly worded email from a generic email account offering you the chance of a lifetime – in exchange for your personal financial data of course.
Remember, if it sounds too good to be true, it probably is.
Graeme Wolfe
IT Security Officer
13/09/2016
Social engineering – the 7 deadly sins that get exploited on line
Posted on: 29 July 2016
By: wolfeg
No Comments »
Filed under: Uncategorized
This month our Information and IT Security Officer Graeme Wolfe, takes a look at the phenomenon of “social engineering” which is behind the majority of successful hacking activities.
From the images promoted by television programmes and movies, many people think of hacking as hi-tech wizardry, cleverly designed software disguised in emails and geeky programmers. However, the reality is usually just an old-fashioned confidence trick, which uses an electronic medium to deliver or maintain the trick.
You could say ‘the con’ has been updated for the modern age where “phishing” and “smishing” are the modern terms used to describe the specific con tricks. All the cons rely upon a set of human characteristics which, with due respect to Hieronymus Bosch, you might think of as the “seven deadly sins” of social engineering.
Apathy
To fall for a confidence trick, or worse, we assume others “must” have taken the necessary steps to keep us secure. Sadly this leads to a lack of awareness, and in the world of the hacker, that is gold dust.
This flaw was perfectly highlighted by the newspaper phone hacking scandals a few years ago. Where certain people’s voice mails could be accessed using the default PIN codes from the network operators. If they had set up a PIN themselves to protect their sensitive information, then they would most likely not have been hacked. This scandal caused many of the mobile service providers to force you to change your PIN when you use their service for the first time.
Another example is if you stay in a hotel and programme your random PIN into the room safe to keep your belongings secure, how many of us check to see if the manufacturers override code has been left in the safe?
Default PIN codes are nearly always 0000 or 1234. Change your PIN codes, if you haven’t already.
Curiosity
Humans are curious by nature. However, naive and uninformed curiosity has caused many casualties. Criminals know we’re curious and they will try to lure us in. If we see an unfamiliar door in a building we frequent, we all wonder where it leads.
If unlocked and there are no signs telling us not to, we might be tempted to open it and find out, but in the online world that might just be a trap waiting for an innocent user to spring it. A researcher for an online security firm built a website that contained a button that said Do Not Press, and was astonished to find that the majority of people visiting the site, actually clicked on it.
Be curious, but exercise a healthy degree of suspicion.
Gullibility
It is often thought of as a derogatory term, but we can all suffer from this sin. We make assumptions. We take others at face value, especially outside of our areas of expertise. Put a uniform (Imperial Storm trooper?!) on someone and we assume they have authority.
Give an email an official appearance by using the correct logo and apparently coming from the correct email address, and we might just assume it’s real, regardless of how silly its instructions might be.
All of this can be easily forged online, so make no assumptions.
Courtesy
We quite rightly all teach our children to be polite. However, politeness does not mean you should not discriminate.
If you do not know something, or you feel something doesn’t feel quite right, then ask someone. This principle is truer than ever in the online world, where we are asked to interact with people and systems in ways with which we can be unfamiliar.
If someone phones you out of the blue and says they are from your bank do you believe them? No. You would phone them back, on a number you obtained elsewhere and check. By the way, it’s best to use a mobile, or different, phone for this; as landlines can remain connected to the person who made the call in the first place and so while you might think you’re phoning the bank on a valid number, you’re just talking to the person who called you.
This happened to me quite recently, when I received calls and texts that looked like they came from my bank. The person I spoke to from the fraud department of my bank, said they wished that all their customers would take similar measures to ensure the identity of the person calling them.
Don’t be afraid to question someone who contacts you and appears to be legitimate. If they are they will understand that you are being cautious and won’t get offended.
Greed
Despite what we’d like to think, we can all be susceptible to greed; even though it might not feel like greed.
Since its inception, the very culture of the web has been to share items for free. Initially this was academic research and pictures of naked ladies! But as the internet was commercialised in the mid to late-1990s, we were left with the impression that we could still find something for nothing.
Nothing is ever truly free online. You have to remember that if you’re not the paying customer, you’re very likely to be the product. In the worst case, you might find that you have taken something onto your machine that is far from what you bargained for.
Many pieces of malware are actively downloaded by people unaware that the “free” product contains a nasty payload, even if it also appears to do what you expected of it.
Have you seen how much access to your personal data many ‘free apps’ require? Do you wonder why, as you click ‘allow’?
Diffidence
People are reluctant to ask strangers for ID, and in the online world it is more important than ever to establish the credentials of those whom you entrust with your personal or sensitive information.
Do not let circumstances lead you to make assumptions about ID.
For example, if someone from “IT support” calls you and asks for your password so they can help fix your problem, how do you know they haven’t called everyone else in the building first until they found you, who really has got a problem?
This is a well-known form of attack. If someone has a problem with proving who they are, you should immediately be suspicious.
Thoughtlessness
Thinking before you act is possibly the most effective means of protecting yourself online. It is all too easy to click that link.
How many of us when reading an apparently valid link in an email would bother to check whether the link is actually valid or whether instead it takes you to a malicious site.
It’s horribly easy to make links look valid, so try hovering your cursor over the link for a few seconds before clicking to see what the real link is, the true link pops up if you give it a moment.
Try to think again and check before clicking on a link.
Conclusion
As cynical as it may sound, the only answer is to practise your A-B-C:
- Assume nothing
- Believe no-one
- Check everything
With more transactions (shopping, banking, etc.) being done online than ever before, you should watch out for those that would exploit the deadly sins.
Don’t give criminals the chance to ruin your on line experience, and remember that a little bit of paranoia goes a long way online.
Graeme Wolfe, Information and IT Security Officer, 21/07/2016
Spam Spam Spam Spam…Now in different flavours.
Posted on: 30 June 2016
By: wolfeg
No Comments »
Filed under: Uncategorized
There have been some interesting developments in the world of spam and malware in the past couple of weeks.
Various organisations1 that monitor internet traffic, have found an alarming increase in the amounts of spam, malware and phishing emails being sent out recently.
They also found that it was not just one type of spam either, there are a number of different ‘flavours’.
Remember the 419 email and letter scams? Typically from Iraq, South Africa or somewhere in West Africa, these advance-fee scams ask for your help to transfer money out of a country in return for a fee. The fraudster requests your bank details for the transfer, and takes the opportunity to empty your account! These scams still seem to be serving up a bad taste in their victims mouths, just when we thought they were off the menu.
There was an increase in the amount of ‘ransomware’ emails being dished out, containing a link which when you click on it allows the scammer to encrypt your files and data, essentially holding your files and data ‘hostage’ until you pay the ransom payment for their decryption. These been rather successful in the past, not only infecting individual’s machines, but also large organisations too. An American hospital got a taste of this and ended up paying thousands of dollars to get their files decrypted.
Scare stories have been emailed to customers of two credential services or password vaults, referring recipients to data breaches by LinkedIn and Tumblr. The emails purporting to be bone-fide support, informed people that their accounts had been hacked and that they needed to re-enter their personal details. These scam emails contained links which directed people to the hackers fake web site, serving up yet another phishing email attack.
There is also new type of fraud that is gaining notoriety, called BEC (Business Email Compromise). Estimates are that tens of thousands of people have been scammed and billions of dollars have been lost world wide. There is such a huge growth in this type of fraud that the FBI issued out a Public Service Announcement. This scam targets employees in an organisation, usually in finance, accounts or procurement, with a message purportedly from a senior finance or accounts manager requesting an urgent payment to be made to a supplier. When the employee takes the bait, the ‘senior manager’ will email and ask for the payment to be made to a different account – the scammers account.
Many of these scams require an increasingly elaborate amount of research and reconnaissance, combined with sophisticated social engineering. As the awareness of scam methods increases and protective measures are taken to avoid them, scammers are devising ever more ingenious ways to trick people. Some are conducting more research into their intended victims, to try to make their messages and requests more appealing.
Just like the canned meat, email spam isn’t going to go away anytime soon. So we all need to be aware and take care when opening attachments, clicking on links or receiving instructions from colleagues that appear to go outside the regular procedures.
Graeme Wolfe, Information and IT Security Officer, 27/06/2016
1 Cloudmark, IC3 and FBI
Windows 10 is calling……what should I do?
Posted on: 1 June 2016
By: wolfeg
No Comments »
Filed under: Uncategorized
This month Graeme Wolfe, Information and IT Security Officer, looks at Windows 10 and at the options for upgrading.
If you use a personal Windows based PC / Laptop / device running Windows 7, 8 or 8.1, you will no doubt have seen the icon in your task bar inviting you, for a limited time, to upgrade to Windows 10 for free.
Your University supplied Windows PC / Laptop will not show this icon as we have suppressed it. We are working on a new ‘build’ to upgrade to Windows 10 at some point, but this has to be done in conjunction with checking that all the various software products on our estate still work as expected with Windows 10 and that there are no conflicts on our network.
I have been asked by a few people whether they should upgrade to Windows 10 on their personal device, or not, especially as there have been some issues raised with the information it gathers and uses about you, plus the deadline imposed by Mircrosoft for a ‘free’ update is July 29th 2016
This really is a personal matter for you and your appetite for moving to a new OS, as there are potential benefits and possible drawbacks to each action. There are many articles and reviews on line, which list the ‘pros’ and ‘cons’ of Windows 10. Just do a search for them if you want to know more, before deciding to take the plunge, or not.
Here are links to a couple of articles to get you started:
I was also asked what the support position was for Windows OS and can reply as follows.
Windows 7 went out of mainstream support in January last year and Windows 8 will join it in January 2018, though they will both continue to receive security patches and updates until they go out of extended support.
Microsoft will be withdrawing extended support for Windows 7 in January 2020 and Windows 8 in January 2023, which may seem a long way off, but there is talk that this may happen earlier than that and this may be a reason why you would want to upgrade to Windows 10.
If you are still unsure as to whether to upgrade or not, but don’t want to make a decision before the July deadline; then you can download and install Windows 10 on your device, then you can ‘roll back’ to your previous OS, Windows 7 or 8. Make sure you take a backup of your files first. You shouldn’t lose any files during the changes, but better to be safe than sorry. This will register you as being a Windows 10 user, so ‘beating’ the deadline and you can go back to Windows 10 when and if the fancy takes you, at a later date.
Graeme Wolfe, Information and IT Security Officer 13/05/2016
Cloud Storage – quick and easy – but for whom?
Posted on: 29 April 2016
By: wolfeg
No Comments »
Filed under: Uncategorized
This month Graeme Wolfe, Information and IT Security Officer has his head in the clouds!
Many people and organisations talk about ‘cloud’ services for data storage and the hosting of services. It sounds impressive and is often hyped up in marketing campaigns. However, the reality is rather more mundane and amounts to merely putting your data or an organisations data or IT service on another organisation’s computer, usually using the internet as the transport method.
So, if you have pictures stored on Instagram or Photo bucket and keep emails, attachments or other files on Google, or Office 365, then you are already using cloud storage services – probably without even realising it!
Two of the great advantages of cloud storage are that you can access your data from anywhere that has an internet connection. Often there is no cost, at least when storing items on a small scale. Cloud storage services can also act as a ‘back up’ to your hard drive or local storage, so you have a copy of things in case your local storage fails.
Two of the problems with cloud storage are that if you don’t have an internet connection you are unable to access your data. Also anyone else who has an internet connection potentially has an opportunity to try and access your data too. Plus you lose physical control over your data and have to rely on someone else to protect it for you.
One question you should be asking yourself when using cloud services is “Do I trust the company who owns the ‘cloud’ to keep my data safe and secure?”
There was a lot of talk in the press last year about celebrity cloud storage accounts (iCloud) being hacked and data (mostly intimate pictures) being stolen. The resulting forensic reports on these attacks showed that many were due to the use of weak passwords, being guessed (or forced) by the attackers.
In my blog dated January 2016 I spoke about the creation and use of secure passwords, for access to any online services. Cloud storage and services are no exception to this, so make sure you have a strong and unique password if you use these services.
You should also be aware that many cloud storage companies will limit their liability for private users (in those terms and conditions we all tick to say we have read and agree to) often to a maximum of $5. Which you may be fine with, if you are storing and sharing some unimportant data. But if the data is worth more than $5 to you, then you should think twice about where you store it. Even if you enter into a commercial (paying a fee) agreement with them, they will limit their liability in the event of lost or corrupted data. But these services should not be used to store, sensitive commercial and personal information on, unless the data is encrypted and the host has no access to the decryption password.
Some modern personal devices will automatically upload data to the cloud for you, so if you don’t want to do this or you want to control what and when it does this, then check the security settings on your device.
Tip: Type “security issues for [your device]” into google and see what comes up. You may be surprised. Then type in “security settings for [your device]” to find out how to keep your data safe.
So in conclusion. Cloud storage can make your life quicker and easier, but take a moment or two to consider putting data security measures in place to make it less quick and easy for any potential attackers.
Graeme Wolfe, Information and IT Security Officer 12/04/2016
Protecting your Wi-Fi Network
Posted on: 30 March 2016
By: wolfeg
No Comments »
Filed under: Uncategorized
The latest security update from our IT Security Officer, Graeme Wolfe, looks at one area of home security you may have overlooked.
How secure is your home?
I’m not talking about the windows and doors, which we all secure and lock before leaving our homes. I’m talking about the other access point into your home and also your life – Wi-Fi
There was a recent article where a technology journalist followed two testers as they hacked into the Wi Fi connected devices in his home. See here
Some 5 years ago, when Google was doing its original Street View surveys, as the cars were driving around taking pictures, they were also ‘listening’ out for Wi-Fi signals. Google got into a lot of bother over this data collection, but it found that nearly half of the Wi-Fi signals they scanned were unsecured. Which highlighted the levels of insecurity on many home wireless networks. See here
These days, with new technologies, more of you may be working from home and connecting your University laptop through your private home wireless network, or you and your family / friends will have many more devices which will want to connect to your Wi Fi.
Your link to the University can be made over a secure connection (by using the University’s’ VPN portal) but you should ensure that you have adequate levels of security on your home wireless network or you could be open to cyber attack or theft / misuse of your broadband to download illegal or pirated material.
Here are some basic general steps that you can take to help secure your wireless access and network, and help keep yourself safe.
- Use encryption on your wireless access points (WAP)
The first and most important way to protect your wireless network is by using encryption. This scrambles data on your wireless network so that only computers with the encryption key can read your communications.
There are two encryption Wi-Fi standards – Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA). However, the problem with WEP is that it’s easily cracked. WPA is much more secure.
If your wireless router and all of your wireless computers and devices support it, WPA2 encryption should be your first choice as it provides the highest level of encryption available.
Use a strong password for your encryption key – for example, a combination of upper and lower case letters, special characters and numbers, ideally totaling 9 characters or more.
- Change the default settings
Always change the details from the manufacturers default settings the device came with.
If you are using the manufacturer’s standard router and security codes that were supplied with the router; remember that this information is likely to be the same for every other router the manufacturer supplies, so it would be a simple matter for a hacker to find out what the standard codes are and then try them to access your network.
Try it for yourself by typing in your routers name, model and the word ‘password’ into a search engine. Often the default username is ‘admin’ and the password is ‘password’.
- Be obscure or disappear altogether!
All wireless routers should have obscure identities. Don’t make it obvious who owns the connection or put in any real information that will reveal your location or name. Be vague and use something like ‘wireless_1’ or ‘router_1’ that doesn’t give anything away. Also change the default setting, which is usually the name and model number of the router. Leaving it like that, helps hackers with item 2 in the list.
Better still don’t broadcast your SSID. Most routers allow you to turn off the sending out of the wireless network name, so you have to know what it is called before you can connect to it. That stops the casual man in the street from finding it and hooking onto it.
- Patch your OS, Install Anti-Virus and a Firewall
All devices that connect to the internet should have their OS patched and have AV running on them.
Firewalls act as a barrier that either blocks information coming through or lets it through. So make sure you have a firewall installed and that it’s switched on. You can view a list of popular software firewalls here
Many routers have a firewall built into them, but a software firewall also helps to protect your personal computer / device, by preventing unauthorised users from accessing your device through the internet or a network, especially when connecting using public Wi-Fi.
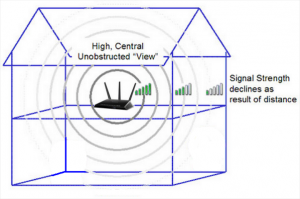
- Position access points carefully
Access points transfer data between your devices, so try to position them away from the outside wall of your building to reduce leakage of radio signals. This will minimise the chance of interception from outside.
- Do you need to use wireless?
Wi-Fi is fine when you are travelling or need access from different locations when working. But when you are at home:
Do you regularly sit in the same place when working?
Are you only a short distance away from your router when using your computer?
Are you using wireless because it was available on the router your ISP provided you with?
Have you considered not using wireless?
Wired access is much faster and very secure in comparison to wireless. Just plug in a network cable from your computer to your router and you are done. Cheap, simple and requires no technical know how. Plus network cables can be up to 100 meters in length before needing to be boosted.
Please note the FixIT Helpdesk are unable to provide specific information or instructions on how to secure your personal network and router at home, as all manufacturers use slightly different systems and settings for their devices.
If you do not feel technically competent to undertake this work, then there are many web sites dedicated to helping people do this, some even have videos and simple step by step guides.
For more information I would either suggest searching online for “How do I secure my network + name and model of router”, or searching for on line manuals on the router manufacturer’s web site, or contacting the supplier of the router directly for technical advice.
Graeme Wolfe – Information and IT Security Officer – 23/03/2016
Online Social Networks (OSN) – A double edged sword.
Posted on: 9 February 2016
By: wolfeg
No Comments »
Filed under: Uncategorized
The latest Patch Tuesday blog from our Information and IT Security Officer, Graeme Wolfe, looks at Online Social Networks and provides some advice and guidance on how to keep yourself out of trouble when using these resources on line.
Online Social Networks. They can be a great way to keep up with your friends and family, share your thoughts, experiences and to express yourself, but there is the potential to end up on the wrong side of a disciplinary hearing, or even the law of the land.
When using the Westminster brand, the University has a policy with guidelines on the safe and correct use of social networks. For your personal use of social media, here is some guidance I have created to help us all keep safer and out of trouble when using OSNs.
Firstly:
Be thoughtful about how you present yourself in OSNs. The lines between public and private, and personal and professional are blurred in OSNs. If you identify yourself as a University employee or are known to be one, you are now connected to your colleagues, the University in general and even our customers. As an employee, you should ensure that any content associated with you is consistent with University policies.
Some of the risks of using OSN’s:
Publishing personal information on your OSN profile may make you susceptible to identity theft
Posting some information about you can also put your personal safety at risk
Phishing attacks can be started by criminals masquerading as genuine companies on an OSN
Social engineering is made easier if you post a lot of personal details on an OSN
OSNs can be used for bullying and harassment online
OSN account hijacking by criminals who use your profile to target your friends
Malicious code (‘malware’) can be spread via OSNs
Third party applications may have more access to your personal details that you are aware of, or happy with
Ways to stay safe when using OSNs:
Don’t post more personal information than is necessary
Protect your friends’ and colleagues’ information
Check your privacy settings
Who are all these people? Are they really your friends? Choose your friends carefully
Be cautious when using third party applications
Read the terms and conditions of the service provider
Think about any information you post
Consider whether your occupation may make you a target
Avoid becoming the victim of phishing attacks, by checking obfuscated URL’s carefully with preview services
Guard against hijack of your own social networking accounts, take care of your log in details
Ensure the computer used to access these sites has anti-virus software running
Try to access them from an account with user privileges only, not administrator privileges
Use ‘strong’ passwords for all online accounts
Personal and business views
As mentioned above, be aware when you are posting anything about your work or the University itself, and that it is clearly marked whether this is the view and opinion of the University or whether it is your own personal view.
Always remember that participation online results in your comments being permanently available and open to being republished in other media.
Stay within the legal framework and be aware that libel, defamation, copyright and data protection laws apply. This means that you should not disclose information, make commitments or engage in activities on behalf of the University, unless you are authorised to do so.
Graeme Wolfe
Information and IT Security Officer
08/02/2016
Password Compromise
Posted on: 14 January 2016
By: wolfeg
No Comments »
Filed under: Uncategorized
This month our Information and IT Security Officer, Graeme Wolfe looks at passwords, and toothbrushes!
Some years ago a Danish colleague of mine likened his password to a toothbrush. I asked him to explain further and he said “Passwords are like toothbrushes, because you use them daily, you should change them regularly, they are personal to you and you would not share them with others”.
Over the past few years there have been a number of high profile security breaches of various internet based services (Sony, LinkedIn, Twitter, Play, Adobe, eBay, Ashley Madison and most recently Talk Talk) where passwords used to access those sites have been compromised.
If you have an online account with any organisation that has suffered a security breach, then at the very least you should immediately change any passwords you use with them – even if you think your account may not have been affected or accessed. Don’t forget to change any passwords to other linked accounts too. e.g. social media links to Facebook, Twitter, Google+.
A recent Ofcom study showed that 1 in 4 people reuse the same password for their online activities and with so many online accounts it’s easy to see why people do this. If you reuse passwords on multiple online accounts, then if one of the online accounts has a security breach, you should also change the password to all other accounts where you reused that password.
This is why it is important that you do not to use your University network password for other external sites and services.
It is also becoming common for criminals to send out ‘phishing’ messages soon after a high profile security breach. They aim to trick people into revealing their details by asking them to click on links in emails to ‘update their details’. You should always avoid links in emails asking you to do this and go directly to the site from a known bookmark or by typing in the web address manually.
Many internet sites and portals will not require you to change your passwords on a regular basis. To maintain security of your account the University requires that staff change their network password every 90 days and for students it is every 365 days. With this in mind you may wish to do the same with accounts you have with other online services by setting yourself a reminder to change those passwords on a regular basis.
There is a lot of good advice and information on passwords and how to keep yourself safe online at these websites:
https://www.getsafeonline.org/protecting-yourself/passwords/
https://www.cyberstreetwise.com/passwords
You can also read information on passwords and internet security on the University IT security webpages https://www.westminster.ac.uk/library-and-it/it-and-software/it-security/strong-passwords
Graeme Wolfe
Information and IT Security Officer
11/01/2016
Cyber-Attacks – the fallout
Posted on: 8 December 2015
By: wolfeg
No Comments »
Filed under: Uncategorized
This month our Information Security Officer, Graeme Wolfe, takes a look at some very high profile cyber-attacks on companies and institutions that took place recently.
Benjamin Franklyn is credited with saying “There are only two things certain in life, death and taxes”. In our digital age, we could add cyber-attacks to that list of inevitability. It seems that every week the media coverage includes a CEO of a large organisation being interviewed over a breach of their security and the loss of customer records, reputation and potentially, the whole business.
At the time this blog was written the V-Tech hack was exposed, where 6.4 million customer records were stolen. You’ll probably have heard about the most recent Talk Talk cyber-attack, where the personal data of 150,000+ customers was stolen over three attacks in 2015. You may also have heard about the denial of service attacks on RBS and the National Crime Agency – both web sites were out of action for hours. You may not have heard about the attacks that occurred across the pond at UCLA (University of California, Los Angeles) – where up to 4 million records were stolen, or T-Mobile US, where up to 15 million records were stolen.
The University itself has also seen various attacks targeted at both staff and students. Staff have been targeted with emails containing attachments marked ‘invoices’ or spreadsheets purportedly coming from ‘scanner@westminster’ our new multi-function device printer machines. Students received a phishing email regarding ‘University grant information’ three times over a period of six-eight weeks.
We have to accept that unless we withdraw completely from the digital age (and become an ‘off grid spoon whittler’ to quote one broadband provider) we will be subjected to these sorts of scams and need to keep our wits about us. Whether that be a suspicious looking attachment from a company you aren’t expecting to hear from, or a link to a website offering you something exciting or tempting, these sorts of attacks will not just go away. In fact, security professionals are seeing an increase in the accuracy, complexity and deviousness underlying these attacks.
We also need to be aware of the fallout from the companies that get hacked. Once our details have been stolen they will be sold on, often many times over. Those that acquire the details will use many further tricks to try and con us to get a return on their ‘investment’. So not only do we have to look out for electronic scams on a day-to-day basis, but when large companies have data stolen, it gives the scammers other opportunities to target us with their tricks including over the telephone and even hard copy mail, depending on what data the hackers can obtain.
Maybe being an off grid spoon whittler doesn’t seem quite so bad now?
Graeme Wolfe
Information and IT Security Officer
07/12/2015
Regular scams
Posted on: 9 September 2015
By: wolfeg
No Comments »
Filed under: Uncategorized
Following last month’s blog post on holiday scams, this month covers some of the other scams that seem to come around at the same time each year.
The scam merry-go-round.
Those of us who follow online security matters have noticed, over time, that some types of scam seem to follow patterns in their appearance. Some appear to crop up over and over again, at different times of the year, like the scam where ‘Microsoft’ are supposedly calling you to fix a problem you never knew you had, especially if you use a Mac! Other scams follow specific patterns and appear at certain times of the year, or in response to certain external influences. With this information in mind we can be on the lookout for these scams.
January and April are common times for HMRC related scams to appear online, either linked to payment deadlines for the self-employed or for the end of the financial year and the need to complete online tax returns. Be very wary of messages purporting to be from the HMRC asking you to confirm information by inputting your personal details to ‘update your account’ or to receive an online tax rebate. HMRC will not contact you in this way.
September, being the start of the academic year, is a popular time for scams related to student loans and higher education fees and charges. Be vigilant of ‘update your account’ messages, as the Student Loan Company will not contact claimants in this way.
Remember, most if not all of the bonafide companies and departments that scammers claim to be contacting you from or on behalf of, clearly state on their web sites that they will not ask you to update or provide personal information via emails.
Summertime brings its own series of events and hence scams.
Holiday related scams, such as credit and debit cards used abroad, foreign exchange related scams, flights, and accommodation and car hire related scams.
Music and other festival based scams around tickets, either ones you may have bought, or offering tickets to events that may be sold out, plus travel and accommodation.
Then there are regular scams that coincide with current affairs or popular causes.
News events can create their own scams, preying on people’s good will when there is a disaster requiring relief aid. So unless you have signed up to an official email or online newsletter, always go to the official charity web sites for details on how to support their causes.
Financial scams linked to, or based around, the mis-selling of financial products such as PPI or CPP. Once such a financial news story breaks, then the scams follow on soon after.
These events provide the scammers with a hook to base their communications as people are aware of the details and are therefore more likely to do what the scammers want them to do.
The rules for dealing with such emails are the same as for any other scam. If you have concerns about how genuine an email or message may be, then contact the company directly. Do not use any links, numbers email addresses or any contact details sent to you in the message. Instead go to the company’s web site from a known bookmark or typed in URL (watch those spellings!) and use the contact information on their web site. Often credit cards will have a fraud line number on the reverse for you to call.
You can check the ‘real’ address of a link by hovering your mouse pointer over the link and the ‘real’ address will pop up in the bottom left corner of your browser window. Try it with this example http://www.westminster.ac.uk/ or this one https://www.barclays.co.uk
Remember the adage ‘if it sounds too good to be true, it usually is’ as scams are trying to influence you into doing something for the benefit of the scammer, not you!
Graeme Wolfe
IT Security Officer
07/09/2015