How valuable is my device and data to a cyber criminal?
Posted on: 28 February 2017
By: wolfeg
No Comments »
Filed under: Uncategorized
This month our Information and IT Security officer, Graeme Wolfe, looks at how any compromised device (PC, laptop, tablet or smartphone) has a value to, and can be used by, cyber criminals.
When I am out and about, talking personal data security with people, I do still hear the following comment: “I don’t have anything sensitive or valuable on my device, so why should I be too worried about IT security?”
The trouble is what may not seem valuable to you, an online email account for example, does have a value to criminals, not a huge one on its own agreed; but if it does become compromised, it can be used to launch ten thousand spam emails in the blink of an eye, then dump it and move to the next one. Which when scaled up to the billions of users on the internet, means there are an awful lot of email accounts that can be used to launch spam attacks and it’s likely that none of them will be blocked by the spam filters on email accounts either.
Let’s say one of those spam mails finds its way to you and you think you know the sender and trust them, so you click on the link and your machine then becomes infected with all sorts of nasty possibilities.
Or maybe the link pretended to be from your bank and took you to a familiar looking web site where you entered all your banking details, effectively handing them to the criminals.
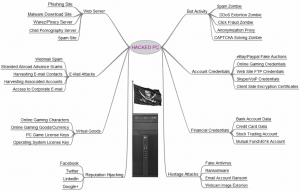
There are a whole host of ways a cyber-criminal can use a compromised device to their advantage and the security expert Brian Krebs (whose web site was attacked last year and was mentioned in my blog post for November) created a graphic which identifies many of the different ways a criminal can use your device to make them money.
Some of these you may have heard of, others will possibly be gobbledegook. But just because you haven’t heard of them doesn’t mean that criminals aren’t using them to take money from unsuspecting people and line their pockets.
Remember, ‘Knowledge is Power’ and if we are all aware of the methods and scams the bad guys use, they are effectively rendered useless.
Graeme Wolfe
Information and IT Security Officer
27/02/2017