Flash, a-ah, saviour of the universe – not for much longer
Posted on: 31 July 2017
By: wolfeg
No Comments »
Filed under: Uncategorized
This month our Information and IT Security officer, Graeme Wolfe, looks at the demise of Adobe Flash and the future of moving images on t’internet.
When I heard that Flash was going to be killed off in 2020, my first thought was for the 1980 movie and Brian Blessed shouting “Flash Gordon’s alive!”
But in reality it is far less entertaining than that. Adobe, the owners of Flash software have decided there will be no more updates and patches for this rather ‘buggy’ and insecure plug in, running in many browsers world-wide.
Until recently Flash ran in browsers, powering videos, games and other animations. But because it was used by so many people, it was a constant target for malware writers trying to get inside it to plant their own code for their own, nefarious, purposes.
It didn’t help that this wasn’t a very secure, or well written piece of software. So regular updates had to be issued out when a vulnerability was exposed.
Newer technologies have superseded Flash, such as HTML5, which is present in just about all modern browsers. Adobe have been slowly removing flash updates and support from other platforms for some time now.
Most ‘Smart’ TV’s will now no longer play Flash based internet video files and games. Android powered smartphones had the support removed around the same time, in 2012. Apple have never liked the product and it was not an option in the App Store. But it did provide a quick and simple way to show moving images in a web browser.
Flash – Gone, but not forgotten.
Graeme Wolfe
Information and IT Security Officer
31/07/2017
GDP aarrgh!
Posted on: 27 June 2017
By: wolfeg
No Comments »
Filed under: Uncategorized
This month our Information and IT Security Officer, Graeme Wolfe, looks at the upcoming changes to Data Protection legislation, explains GDPR and considers the impact for our University.
InfoSec17, the annual Security exhibition and conference, returned to London in June, as with previous years there continues to be two constants.
The first being each event has seen more visitors, exhibitors, new products, presentations, workshops and ideas on display. Proving security is a continually growing market which should not be ignored and the issues around it will not disappear anytime soon.
The second is that there is often a theme that the exhibitors focus on, to use to promote their products. This year saw two themes given equal exposure, Ransomware and General Data Protection Regulation [GDPR].
If you have been following my recent blogs, or seen the news, then you will be aware of the recent high profile ransomware attacks on corporations around the world, including the NHS and most recently the password attack on Parliament. But you may not have heard about the introduction of GDPR, which will have a huge impact on how we all process, store and share data in the future.
Currently all organisations in the UK that handle sensitive personal data are bound by the Data Protection Act 1998 (DPA). But in less than a year [25 May 2018 to be precise], this will be replaced by the General Data Protection Regulation [GDPR], which will apply across the European Union, unifying data protection rules.
GDPR:
- Places more responsibility on organisations, large and small, to ensure they handle personal data in a safe and secure manner.
- Redefines what is personal data and the accountability and governance that must go along with its everyday use and storage.
- Applies to both electronic and hard copy data, new and existing systems, as well as archived materials.
- Defines new roles and responsibilities in organisations and will bring some big changes with it.
One of the big changes, is the level of fines that can be imposed for breaching the GDPR. Currently the maximum fine for breaching the DPA is £500,000, this is to be increased to a maximum of 20 Million Euros or 4% of global turnover. For small organisations that lose personal data, any fine can make a large impact on their budgets, however, the increases that have been put in place, will impact on large multinationals too, and ensure they also take notice of these rules.
The University of Westminster’s Compliance team have been working on getting us ready for GDPR for some time. There is still much work to be done, but speaking to visitors and exhibitors at InfoSec17, we appear to be ahead of many other organisations in this matter.
Graeme Wolfe
Information and IT Security Officer
26/06/17
Recent malware attacks and some predictions
Posted on: 30 May 2017
By: wolfeg
No Comments »
Filed under: Uncategorized
This month our Information and IT Security Officer, Graeme Wolfe, looks at the recent rise in high profile malware and considers the future of such attacks.
The first week in May saw a new form of attack take place, one where the attackers were using a very realistic looking piece of malware, which appeared to be a genuine Google Docs application, but was in fact a sophisticated piece of malware. This caught a lot of people out, before it was identified as malware and the exploit was shut down. (See note 1 below for more advice)
The second week in May saw the well documented ‘WannaCry’ Ransomware attack that affected the NHS and many other organisations, both commercial and public sector, across the world. (See note 2 below for more advice)
Fortunately, the third and fourth weeks in May appeared to be fairly quiet, though the SANS institute’s Internet Storm Centre, shows a fairly consistent level of ongoing attacks for May, with a couple of spikes for the above two attacks. Ongoing attacks generally have a lower profile and impact, so don’t tend to make the news.
Last month I wrote about the importance of applying security patches, after the theft of a number of ‘zero day’ exploits that were stolen from the NSA recently, and also of being aware of your actions on line. It would appear to have been somewhat prophetic.
This month I am going to make a prediction. These two attacks are not the last such attacks we will experience over the coming months and years. While it is cheap to mount these attacks and there is profit to be made, then they will keep on coming. ‘WannaCry’ used the ‘Eternal Blue’ exploit from the stolen NSA toolkit. So keep your eyes open for ‘EsteemAudit’ (another stolen NSA exploit) or variants thereof, in the not too distant future.
While organisations (and individuals) continue to run unpatched and insecure systems and there are criminals out in the “ether” who can exploit these vulnerabilities for financial gain, then these sorts of attacks will continue and they will increase, in number, in severity and in impact.
This sort of malicious activity used to be the preserve of those with technical backgrounds, who tended to perform their attacks to prove their ability amongst their peers, or to make a point or political statement.
But now it is possible to go to online marketplaces, where you can buy all the components needed to perform similar types of attacks, in an easy to use format, including lists of names and email addresses or other details, a bit like buying something from eBay and just like on eBay, the sellers have feedback ratings and rankings, many even offer 24 hour support lines and money back guarantees! Scams and malware have moved from a fringe activity into the mainstream.
This means that it is possible for many criminals, with just a little technical savvy, to perform attacks and make money from the comfort of their own homes. Which is far easier than robbing a bank, or burgling a house, or whatever other activities criminals get up to. Plus, with easily available advice on hiding their locations and identities, they can get away with their crimes with little or no chance of ever being caught. So it is no surprise that cyber crime has seen the fastest rates of growth of any crime in the past few years and that doesn’t look set to change anytime soon.
Graeme Wolfe
Information and IT Security Officer
30/05/2017
Note 1 – If you did click through the links and pressed yes to the request for permissions from the Google malware, then it is likely that the attackers will have access to all your Google address lists and the ability to send out the same message to all your contacts.
If you were a victim of this fraud, then just changing your password would not be sufficient as you will need to revoke the permissions given to the rogue Google Docs app.
Google did fix the problem within a day and prevented the spread of any more emails. They added that this only affected 0.1% of their users, but with over a Billion users world-wide, that is in excess of One Million Accounts that were compromised. Which puts some of the earlier attacks on Yahoo and other web mail accounts, in the shade.
Note 2 – Windows XP, Vista or Windows 8 If you are running a home device with one of these, then you should consider replacing them with a more modern version. There is no longer any official support for this software and as time goes on, they will not get any safer.
If you are running Windows 7 or 8.1 then make sure you have your updates turned ‘On’ and that you install the updates provided.
Windows updates – what you need to know
Posted on: 24 April 2017
By: wolfeg
No Comments »
Filed under: Uncategorized
This month, our Information and IT Security officer, Graeme Wolfe, looks at the latest updates for Windows machines and why they are important.
One of the original intentions of this blog was to remind you to check and apply any new security patches that have been released in the past month.
These are usually released on the second Tuesday of the month, or ‘Patch Tuesday’ as it is known.
This month (April) there is a selection of patches for Windows and Office that will patch what are known as ‘zero day attacks’. These are when a security flaw becomes known to the hacking community, but the fixes to close the flaw have yet to be released (and of course to be downloaded and applied to each device)
Your University supplied Windows laptop and desktop devices will be sent the appropriate patches automatically. We will also check these patches do not cause any instability in the standard software on your device/s. Be aware that these patches may have installed the last time you shut down, when updates are still to be installed you will see an exclamation mark! on the shutdown button (on the start menu).
If you have any personal devices running Windows and Office and they are not set up to receive automatic updates, then you should download and install these patches each month. If you receive an on screen reminder then follow these simple instructions.
The Windows reminder will often ask if you want to download and install the updates, so click on Yes.
To check you have the latest updates, click on ‘start’ then ‘all programs’
In the list of programs there will be a ‘Windows update’ icon, click on that
You will then get an on screen Window displaying the current status of your updates.
Graeme Wolfe
Information and IT Security Officer
24/04/2017
Encryption, why it is Important
Posted on: 28 March 2017
By: wolfeg
No Comments »
Filed under: Uncategorized
Following on from last month’s blog, about how cyber criminals can use your compromised device to further their own ends, this month our Information and IT Security Officer, Graeme Wolfe, looks at encryption and how it is used to keep your online data and information safe and secure.
Encryption, in some form, has been around for many years. Julius Caesar used a simple form of encryption in his messages to his armies, to try to prevent enemies discovering his plans. The German enigma machine of WWII was a huge leap forwards in secure communications and drove the development of the modern computer age.
50 Years ago, two graduates at Stanford University, Whitfield Diffie and Martin Hellman produced detailed studies on how you could easily send a secure message to a person, so only they (the recipient) could decode it, without having to exchange any details that could be intercepted by a third party. This involved complex mathematics, based on prime numbers and the work they published went on to provide a secure foundation for the digital world we all now live in.
Within our everyday online activities, every time you put your password or credit card details into a web site, open a VPN (Virtual Private Network) to connect to work securely, or send some personal or sensitive information in a secure email, encryption means you can be sure that the only person who can read any data contained in the secure connection, is the recipient.
It also enables web sites to certify they are who they say they are, and not some scammers or a phishing site.
It is fair to say that without this mathematical encryption technology, the internet as we know it, and e-commerce in particular, just wouldn’t work.
If you send or receive personal, sensitive information for your work and don’t currently have an encrypted email option, or regularly work away from the office and could use a secure VPN to connect up to work, please contact the Service Desk, who can advise you how these may be obtained. Or if you would just like to know more about encryption, then feel free to contact me.
Graeme Wolfe
Information and IT Security Officer
28/03/2017
How valuable is my device and data to a cyber criminal?
Posted on: 28 February 2017
By: wolfeg
No Comments »
Filed under: Uncategorized
This month our Information and IT Security officer, Graeme Wolfe, looks at how any compromised device (PC, laptop, tablet or smartphone) has a value to, and can be used by, cyber criminals.
When I am out and about, talking personal data security with people, I do still hear the following comment: “I don’t have anything sensitive or valuable on my device, so why should I be too worried about IT security?”
The trouble is what may not seem valuable to you, an online email account for example, does have a value to criminals, not a huge one on its own agreed; but if it does become compromised, it can be used to launch ten thousand spam emails in the blink of an eye, then dump it and move to the next one. Which when scaled up to the billions of users on the internet, means there are an awful lot of email accounts that can be used to launch spam attacks and it’s likely that none of them will be blocked by the spam filters on email accounts either.
Let’s say one of those spam mails finds its way to you and you think you know the sender and trust them, so you click on the link and your machine then becomes infected with all sorts of nasty possibilities.
Or maybe the link pretended to be from your bank and took you to a familiar looking web site where you entered all your banking details, effectively handing them to the criminals.
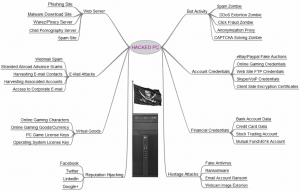
There are a whole host of ways a cyber-criminal can use a compromised device to their advantage and the security expert Brian Krebs (whose web site was attacked last year and was mentioned in my blog post for November) created a graphic which identifies many of the different ways a criminal can use your device to make them money.
Some of these you may have heard of, others will possibly be gobbledegook. But just because you haven’t heard of them doesn’t mean that criminals aren’t using them to take money from unsuspecting people and line their pockets.
Remember, ‘Knowledge is Power’ and if we are all aware of the methods and scams the bad guys use, they are effectively rendered useless.
Graeme Wolfe
Information and IT Security Officer
27/02/2017
Be careful what you wish for…
Posted on: 20 January 2017
By: wolfeg
No Comments »
Filed under: Uncategorized
This month Graeme Wolfe, our Information and IT Security Officer, looks at ‘smart home assistants’ and how to ensure you set your default accounts correctly, so that your ‘wished for’ list does not come true with all sorts of unexpected consequences.
You may have seen the launch last year of ‘smart home assistants’ from Amazon (Echo) and Google (Home) which employ Artificial Intelligence to listen out for your instructions and then act upon them. Saying “play this piece of music” or “remind me I have a meeting this afternoon” is fairly simple, but they can also order things online for you and that is where the problems can start.
An example of this, was to the surprise of one owner of a ‘smart home assistant’ when a dolls house arrived from Amazon that they hadn’t ordered. It turned out that their young daughter had ‘wished’ for one and the home assistant picked this up and dutifully placed an order for one. Later on, this made it to the local news in San Diego and when the TV presenter broadcast the words the child had spoken, there were ‘smart home assistants’ all over the local area that heard the request from the television and went and ordered up dolls houses as well!
It turns out that these ‘smart home assistants’ are unable to discriminate between your voice, that of your children, guests and even those coming from television or radio. The default setting on the Amazon device is to enable voice purchases. If you own one of these devices, be sure to go into the settings and make sure that you have changed the defaults to ones that suit your particular needs.
Graeme Wolfe
Information and IT Security Officer
19/01/17
5 Myths about the internet and security
Posted on: 15 December 2016
By: wolfeg
No Comments »
Filed under: Uncategorized
The latest blog from our Information and IT Security Officer, Graeme Wolfe, looks at some myths around internet security, providing further advice and guidance on ways to keep yourself and your family safe and secure, especially in the run up to Christmas, when many of us are likely to be internet shopping and undertaking other online activities.
5 Myths about the internet and security:
I often get asked questions about the safe use of the ‘internet’, the threats and the myths attached to using the internet. Like the programme on the Discovery channel, here are some security myths that are BUSTED!
- If I visit a compromised web site, my computer can only be infected if I agree to download or install malicious software. This is not always the case, some infected sites use background software that your computer will automatically run, to install their malware. To protect your computer from such attacks ensure you have up to date anti-virus software or malware scanners installed.
- Only ‘disreputable’ sites will contain malware. Hackers can find a way into any ‘reputable’ site and use it to host their malware, especially if that site doesn’t have good security protocols and measures, or has not been properly security tested. Just because a link takes you to a recognisable site, always be careful about what you enter or download. Better still, go to the site from a known bookmark or web address.
- I am too small a ‘fish’ to be of interest to hackers. Never underestimate the targeting ability of criminals and activists. Every single device that is compromised can be added to the network of computers used to support illegal activity or attack other sites and services.
- I have very little of any value to a hacker on my device. There is potential value for all information stored on your device as follows:
- Your address book contains details of ‘live’ email accounts that can be targeted or sold on
- Browser’s and memory can retain a lot of personal data about you and your browsing habits, your ‘Digital Identity’, criminals can use this information
- You may not think your data is valuable, but there are those who do and will try to obtain it from you (see myth 3 above).
5. My device is not one targeted by hackers. In the past this may have been true, but the massive rise in new technology, platforms and devices, combined with the ease by which an attacker can launch an attack, means that ANY device connected to the internet can be considered a target (see myths 3 and 4 above and my blog from last month).
So if any of you remember the programme ‘Hill Street Blues’, in the words of Sgt Phil Esterhaus “Let’s be careful out there!”
Graeme Wolfe
Information and IT Security Officer
09/12/2016
The Internet of Things…Smart Devices and how they are used in cyber-attacks
Posted on: 30 November 2016
By: wolfeg
No Comments »
Filed under: Uncategorized
This month we are looking at smart devices that connect to the internet and how they can be (and have been) easily compromised for use by criminals and activists.
Recently in the media you may have heard about the ‘Internet of Things’ (IoT), Smart Devices and how they have been used in recent cyber-attacks.
IoT simply refers to everyday objects or devices (both consumer and business) that have an internet connection and are able to send and receive data, usually without any human involvement. These items could be anything from fridges, TV’s, printers, baby monitors, CCTV cameras, even cars and buildings.
Unfortunately many of these devices are manufactured and distributed with little or no inbuilt security, often having a default standard password set up on each device. This is why we ensure anything that connects to the internet has the appropriate security built-in and that it is activated.
The Internet Storm Centre at the SANS institute, regularly tests the vulnerability of devices that are connected to the internet that have not been correctly patched or secured. Their testing regularly find’s that devices are discovered by ‘hackers’ and quickly compromised in as little as 5 minutes after connection!
You may not have heard of the recent cyber-attacks on websites that try to expose these ‘hackers’ and educate us on the need for security (krebsonsecurity). Recent attacks on Dyn, the company that manages the routing of a large part of the internet, affected many well-known sites and made them inaccessible, such as Twitter, Spotify, Netflix, Sound Cloud, PayPal, Reddit and parts of the Amazon web services.
The attack Dyn suffered was called a ‘Distributed Denial of Service’ attack (DDoS) which interrupted their Domain Name System (DNS) services, which is the way to translate a web address into an IP address that a computer understands, and then continued to attack the Dyn systems. This meant that the companies named above, who used the services of Dyn to connect and route web traffic, effectively dropped off of the internet and people were unable to connect to their web pages.
It is also suspected that a similar method was used, earlier this month, to affect the internet connections for the entire country of Liberia.
Devices that were classified as belonging to the IoT were identified as the source of the attack on Krebsonline and Dyn, many had been compromised with a well-known piece of malware called Mirai. Due to the seriousness and implications for all users of the internet, the US Government security arm, National Institute for Standards and Technology (NIST), has issued technical details for manufacturers on how to build their devices so they are resilient and trustworthy.
But until these new guidelines are incorporated into IoT devices, if you have any devices that have internet connectivity, from a home printer to a baby monitor or CCTV unit, then if possible you should always change the default passwords that come with them. Otherwise you could find your ‘fridge starts a cyber attack on your TV!
Graeme Wolfe
Information and IT Security Officer
30/11/16
Malware attacks!
Posted on: 31 October 2016
By: wolfeg
No Comments »
Filed under: Uncategorized
Following on from last month’s post about regular scams and my recent blog about spam; if you follow the news you will have seen that in the intervening few months there have been further reports about cyber security issues. These have involved some big names and big numbers, for example:
- Yahoo – 500 million accounts compromised!
- Talk Talk –they were fined £400,000 by the Information Commissioner for breaches of the Data Protection Act relating to the hundreds of thousands of accounts that were compromised.
The key advice from all the companies in these situations is to change your log in password and monitor your accounts for at least a couple of months, for any unusual activity.
You may say, ‘So what? I don’t use any of those services, so why should I worry?’ Well, Yahoo provide email services for both Sky and BT, so you may find you are indirectly affected. Plus, according to the Symantec Security Insights Report, 1 in 113 emails contains malware and an increase in activity saw over one million new malware variants being created each day in August and September. So it’s only a matter of time before one crosses your path – if it hasn’t already. In addition, these attacks are not restricted to large online service providers and attacks can come from places a lot closer to home.
Cybersecurity firm SentinelOne contacted 71 UK universities asking if they had been attacked by Ransomware (see here for an explanation of Ransomware). Of the 58 which replied, 23 said they had been attacked in the last year. In particular, Bournemouth University, which boasts a cybersecurity centre, has been hit 21 times in the last 12 months.
The attacks are not limited to any particular area of business either, as 28 NHS Trusts said they had also been affected.
What this does show is that no one who operates online, in any way, is truly safe. But by being vigilant and thinking before acting, it is possible to greatly reduce the risk of being a victim of cyber-crime.
In addition to the guidance on the University’s IT Security pages on spotting malware attacks, it can be hard to know if an email, or other communication, is genuine or trying to extract more information from you. But in principle, if you are asked to click on a link in an email, then ‘re enter’ your details into a site, or are told that you have to act quickly to prevent something happening, then it’s probably a scam. Genuine organisations will not ask you to ‘re enter’ your information, or share your password or PIN with anyone from their organisation. Going to the security pages of their website will often confirm this. Also checking the return / sending email address an email was sent from can provide clues for you. Many scammers will produce emails or messages that may look like they have come from a genuine company, but on closer inspection appear to come from Yahoo or other webmail services. Plus email links in messages may not take you to the URL that is often shown in the text. So obviously they will be highly suspicious.
Graeme Wolfe
Information Security Officer
25/10/16